Nmap是一个非常强大的工具,今天我们来看一下这30个常用的例子:
N map is short for Network Mapper. It is an open source security tool for network exploration, security scanning and auditing. However, nmap command comes with lots of options that can make the utility more robust and difficult to follow for new users.
Nmap是Network Mapper的缩写,他是一个开源的网络检测,扫描,审计工具,然而,nmap有非常多的选项,这让nmap非常的功能强大和健壮,当然这也给新用户造成了一定的困难
The purpose of this post is to introduce a user to the nmap command line tool to scan a host and/or network, so to find out the possible vulnerable points in the hosts. You will also learn how to use Nmap for offensive and defensive purposes.
这篇文章的目的是介绍如何使用nmap来扫描一个主机或者网络,以发现可能被攻击的地方。你将从本文章中学会如何使用Nmap,无论是用于攻击或者防御
More about nmap
Nmap的更多信息:
From the man page:
从Nmap的说明文档中我们得到:
Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap(“Network Mapper”)是一个开源的,用来检测网络和审计安全的。它被设计为快速扫描比较大的网络,当然,它在扫描单台主机上表现的也非常号。Nmap使用原始的IP包通过一个中新颖的方式来判断主机是否存活在指定网络,这些主机提供了那些服务及具体服务的版本,以及操作系统的版本,防火墙的版本,还有其它一大堆的东西。虽然nmap是用来做安全审计的,但是很多网络管理员发现nmap在网络的日常任务上也非常又用,例如 管理服务的升级规划,监控主机和服务的启动时间等。
It was originally written by Gordon Lyon and it can answer the following questions easily:
这个是Gordon Lyon写的,这些内容可以很容易的回答如下的问题:
1、What computers did you find running on the local network? 本地局域网中的计算器?
2、What IP addresses did you find running on the local network?本地局域网中使用的IP?
3、What is the operating system of your target machine?目标主机使用的操作系统?
4、Find out what ports are open on the machine that you just scanned?目标主机对外开放的端口?
5、Find out if the system is infected with malware or virus.目标主机是否被病毒感染
6、Search for unauthorized servers or network service on your network.查找未被授权的主机或者服务
7、Find and remove computers which don’t meet the organization’s minimum level of security.查找那些没有符合最低安全标准的远程主机
Sample setup (LAB)
测试环境撘建
Port scanning may be illegal in some jurisdictions. So setup a lab as follows:、
端口扫描在某些地区是违规的,所以我们按照下图设置我们的实验环境
+---------+
+---------+ | Network | +--------+
| server1 |-----------+ swtich +---------|server2 |
+---------+ | (sw0) | +--------+
+----+----+
|
|
+---------+----------+
| wks01Linux/OSX |
+--------------------+
Where,
· wks01 is your computer either running Linux/OS X or Unix like operating system. It is used for scanning your local network. The nmap command must be installed on this computer.(wks01是你的主机,安装的系统是linux或者Unix系列的开源系统,这台主机用来扫描本地网络,所以Nmap需要在这台机器上安装好)
· server1 can be powered by Linux / Unix / MS-Windows operating systems. This is an unpatched server. Feel free to install a few services such as a web-server, file server and so on.(server1是目标主机,没有任何的防御开放,你可以随便安装及个服务,例如httpd或者文件服务)
· server2 can be powered by Linux / Unix / MS-Windows operating systems. This is a fully patched server with firewall . Again, feel free to install few services such as a web-server, file server and so on.(server2目标主机2,被防火墙保护,和server1一样,随意安装及个服务)
· All three systems are connected via switch.(所有的机器通过交换器链接)
How do I install nmap?
如何安装Nmap?
See:
具体根据不同版本选择不同大安装方式:
1、Debian / Ubuntu Linux: Install nmap Software For Scanning Network
2、CentOS / RHEL: Install nmap Network Security Scanner
3、OpenBSD: Install nmap Network Security Scanner
#1: Scan a single host or an IP address (IPv4)
#1:扫描一个单独的主机或者一个单独的IP地址(IPv4)
### Scan a single ip address ###
nmap 192.168.1.1
## Scan a host name ###
nmapserver1.cyberciti.biz
## Scan a host name with more info###
nmap -v server1.cyberciti.biz
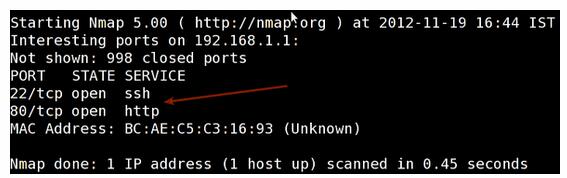
Sample outputs:
输出如下:
Fig.01: nmap output
#2: Scan multiple IP address or subnet (IPv4)
#2:扫描多个IP或者一个子网:
nmap 192.168.1.1 192.168.1.2 192.168.1.3
## works with same subnet i.e. 192.168.1.0/24
nmap 192.168.1.1,2,3
You can scan a range of IP address too:
你可以扫描一个ip段
nmap 192.168.1.1-20
You can scan a range of IP address using a wildcard:
你可以使用统配符来指定ip
nmap 192.168.1.*
Finally, you scan an entire subnet:
你也可以扫描整个子网段
nmap 192.168.1.0/24
#3: Read list of hosts/networks from a file (IPv4)
从一个文件中读取主机列表或者网络列表
The -iL option allows you to read the list of target systems using a text file. This is useful to scan a large number of hosts/networks. Create a text file as follows:
cat > /tmp/test.txt
Sample outputs:
server1.cyberciti.biz
192.168.1.0/24
192.168.1.1/24
10.1.2.3
localhost
The syntax is:、
具体的命令:
nmap -iL /tmp/test.txt
#4: Excluding hosts/networks (IPv4)
#4排除某些主机或者网段(IPv4)
When scanning a large number of hosts/networks you can exclude hosts from a scan:
当我们扫描一个很大的网段的时候,我们可以排除一些主机
nmap 192.168.1.0/24 --exclude 192.168.1.5
nmap 192.168.1.0/24 --exclude 192.168.1.5,192.168.1.254
OR exclude list from a file called /tmp/exclude.txt
我们也可以通过一个文件来读取我们需要排除的主机
nmap -iL /tmp/scanlist.txt --excludefile /tmp/exclude.txt
#5: Turn on OS and version detection scanning script (IPv4)
#5打开系统版本检测
nmap -A 192.168.1.254
nmap -v -A 192.168.1.1
nmap -A -iL /tmp/scanlist.txt
#6: Find out if a host/network is protected by a firewall
#6确定主机或者网络是否被防火墙保护
nmap -sA 192.168.1.254
nmap -sAserver1.cyberciti.biz
#7: Scan a host when protected by the firewall
#7:扫描一个主机如果这个主机被防火墙保护
nmap -PN 192.168.1.1
nmap -PNserver1.cyberciti.biz
#8: Scan an IPv6 host/address
#8:扫描IPv6主机/地址
The -6 option enable IPv6 scanning. The syntax is:
-6 选项让我们开启了IPv6的扫描
nmap -6 IPv6-Address-Here
nmap -6 server1.cyberciti.biz
nmap -6 2607:f0d0:1002:51::4
nmap -v A -6 2607:f0d0:1002:51::4
#9: Scan a network and find out which servers and devices are up and running
#9:扫描一个网络并查找所有存活的设备
This is known as host discovery or ping scan:
通过ping来检查
nmap -sP 192.168.1.0/24
Sample outputs:
输出接过:
Host 192.168.1.1 is up (0.00035s latency).
MACAddress: BC:AE:C5:C3:16:93 (Unknown)
Host 192.168.1.2 is up (0.0038s latency).
MACAddress: 74:44:01:40:57:FB (Unknown)
Host 192.168.1.5 is up.
Hostnas03 (192.168.1.12) is up (0.0091s latency).
MACAddress: 00:11:32:11:15:FC (SynologyIncorporated)
Nmapdone: 256 IPaddresses (4 hostsup) scannedin 2.80 second
#10: How do I perform a fast scan?
#10:如何进行一个快速的扫描?
nmap -F 192.168.1.1
#11: Display the reason a port is in a particular state
#11:显示端口处于特殊状态的原因(这个有点奇怪,翻译的感觉有点怪)
nmap --reason 192.168.1.1
nmap --reasonserver1.cyberciti.biz
#12: Only show open (or possibly open) ports
#12:紧紧显示开启的端口(可能开启的)
nmap --open 192.168.1.1
nmap --openserver1.cyberciti.biz
#13: Show all packets sent and received
显示所有的发送和接受的包
nmap --packet-trace 192.168.1.1
nmap --packet-traceserver1.cyberciti.biz
14#: Show host interfaces and routes
显示主机的接口和路由
This is useful for debugging ( ip command or route command or netstat command like output using nmap)
这个用来debug非常有效
nmap --iflist Sample outputs: StartingNmap 5.00 ( http://nmap.org ) at 2012-11-27 02:01 IST ************************INTERFACES************************ DEV (SHORT) IP/MASK TYPE UPMAC lo (lo) 127.0.0.1/8 loopback up eth0 (eth0) 192.168.1.5/24 ethernet upB8:AC:6F:65:31:E5 vmnet1 (vmnet1) 192.168.121.1/24 ethernet up 00:50:56:C0:00:01 vmnet8 (vmnet8) 192.168.179.1/24 ethernet up 00:50:56:C0:00:08 ppp0 (ppp0) 10.1.19.69/32 point2pointup **************************ROUTES************************** DST/MASK DEV GATEWAY 10.0.31.178/32 ppp0 209.133.67.35/32 eth0 192.168.1.2 192.168.1.0/0 eth0 192.168.121.0/0 vmnet1 192.168.179.0/0 vmnet8 169.254.0.0/0 eth0 10.0.0.0/0 ppp0 0.0.0.0/0 eth0 192.168.1.2 |
#15: How do I scan specific ports?
如何扫描特殊端口
nmap -p [port] hostName ## Scan port 80 nmap -p 80 192.168.1.1 ## Scan TCP port 80 nmap -p T:80 192.168.1.1 ## Scan UDP port 53 nmap -p U:53 192.168.1.1 ## Scan two ports ## nmap -p 80,443 192.168.1.1 ## Scan port ranges ## nmap -p 80-200 192.168.1.1 ## Combine all options ## nmap -p U:53,111,137,T:21-25,80,139,8080 192.168.1.1 nmap -p U:53,111,137,T:21-25,80,139,8080 server1.cyberciti.biz nmap -v -sU -sT -p U:53,111,137,T:21-25,80,139,8080 192.168.1.254 ## Scan all ports with * wildcard ## nmap -p "*" 192.168.1.1 ## Scan top ports i.e. scan $number most common ports ## nmap --top-ports 5 192.168.1.1 nmap --top-ports 10 192.168.1.1 |
Sample outputs:
输出结果
StartingNmap 5.00 ( http://nmap.org ) at 2012-11-27 01:23 IST
Interestingportson 192.168.1.1:
PORT STATE SERVICE
21/tcp closedftp
22/tcp open ssh
23/tcp closedtelnet
25/tcp closedsmtp
80/tcp open http
110/tcp closedpop3
139/tcp closednetbios-ssn
443/tcp closedhttps
445/tcp closedmicrosoft-ds
3389/tcpclosedms-term-serv
MACAddress: BC:AE:C5:C3:16:93 (Unknown)
Nmapdone: 1 IPaddress (1 hostup) scannedin 0.51 seconds
#16: The fastest way to scan all your devices/computers for open ports ever
最快的方式来扫描所有的设备打开的端口
nmap -T5 192.168.1.0/24
#17: How do I detect remote operating system?
如何检测一个远端操作系统
You can identify a remote host apps and OS using the -O option :
我们可以通过-O这个选项来检测远端操作系统
nmap -O 192.168.1.1
nmap -O --osscan-guess 192.168.1.1
nmap -v -O --osscan-guess 192.168.1.1
Sample outputs:
输出:
StartingNmap 5.00 ( http://nmap.org ) at 2012-11-27 01:29 IST NSE: Loaded 0 scriptsfor scanning. InitiatingARPPingScanat 01:29 Scanning 192.168.1.1 [1 port] CompletedARPPingScanat 01:29, 0.01s elapsed (1 totalhosts) InitiatingParallelDNSresolutionof 1 host. at 01:29 CompletedParallelDNSresolutionof 1 host. at 01:29, 0.22s elapsed InitiatingSYNStealthScanat 01:29 Scanning 192.168.1.1 [1000 ports] Discoveredopenport 80/tcpon 192.168.1.1 Discoveredopenport 22/tcpon 192.168.1.1 CompletedSYNStealthScanat 01:29, 0.16s elapsed (1000 totalports) InitiatingOSdetection (try #1) against 192.168.1.1 RetryingOSdetection (try #2) against 192.168.1.1 RetryingOSdetection (try #3) against 192.168.1.1 RetryingOSdetection (try #4) against 192.168.1.1 RetryingOSdetection (try #5) against 192.168.1.1 Host 192.168.1.1 is up (0.00049s latency). Interestingportson 192.168.1.1: Not shown: 998 closedports PORT STATESERVICE 22/tcpopen ssh 80/tcpopen http MACAddress: BC:AE:C5:C3:16:93 (Unknown) Devicetype: WAP|generalpurpose|router|printer|broadbandrouter Running (JUSTGUESSING) : LinksysLinux 2.4.X (95%), Linux 2.4.X|2.6.X (94%), MikroTikRouterOS 3.X (92%), Lexmarkembedded (90%), Enterasysembedded (89%), D-LinkLinux 2.4.X (89%), NetgearLinux 2.4.X (89%) AggressiveOSguesses: OpenWrtWhiteRussian 0.9 (Linux 2.4.30) (95%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (94%), OpenWrtKamikaze 7.09 (Linux 2.6.22) (94%), Linux 2.4.21 - 2.4.31 (likelyembedded) (92%), Linux 2.6.15 - 2.6.23 (embedded) (92%), Linux 2.6.15 - 2.6.24 (92%), MikroTikRouterOS 3.0beta5 (92%), MikroTikRouterOS 3.17 (92%), Linux 2.6.24 (91%), Linux 2.6.22 (90%) NoexactOSmatchesfor host (If youknowwhatOSis runningonit, seehttp://nmap.org/submit/ ). TCP/IPfingerprint: OS:SCAN(V=5.00%D=11/27%OT=22%CT=1%CU=30609%PV=Y%DS=1%G=Y%M=BCAEC5%TM=50B3CA OS:4B%P=x86_64-unknown-linux-gnu)SEQ(SP=C8%GCD=1%ISR=CB%TI=Z%CI=Z%II=I%TS=7 OS:)OPS(O1=M2300ST11NW2%O2=M2300ST11NW2%O3=M2300NNT11NW2%O4=M2300ST11NW2%O5 OS:=M2300ST11NW2%O6=M2300ST11)WIN(W1=45E8%W2=45E8%W3=45E8%W4=45E8%W5=45E8%W OS:6=45E8)ECN(R=Y%DF=Y%T=40%W=4600%O=M2300NNSNW2%CC=N%Q=)T1(R=Y%DF=Y%T=40%S OS:=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%R OS:D=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W= OS:0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID OS:=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Uptimeguess: 12.990 days (sinceWedNov 14 01:44:40 2012) NetworkDistance: 1 hop TCPSequencePrediction: Difficulty=200 (Goodluck!) IPIDSequenceGeneration: Allzeros Readdatafilesfrom: /usr/share/nmap OSdetectionperformed. Pleasereportanyincorrectresultsathttp://nmap.org/submit/ . Nmapdone: 1 IPaddress (1 hostup) scannedin 12.38 seconds Rawpacketssent: 1126 (53.832KB) | Rcvd: 1066 (46.100KB) See also: Fingerprinting a web-server and a dns server command line tools for more information. |